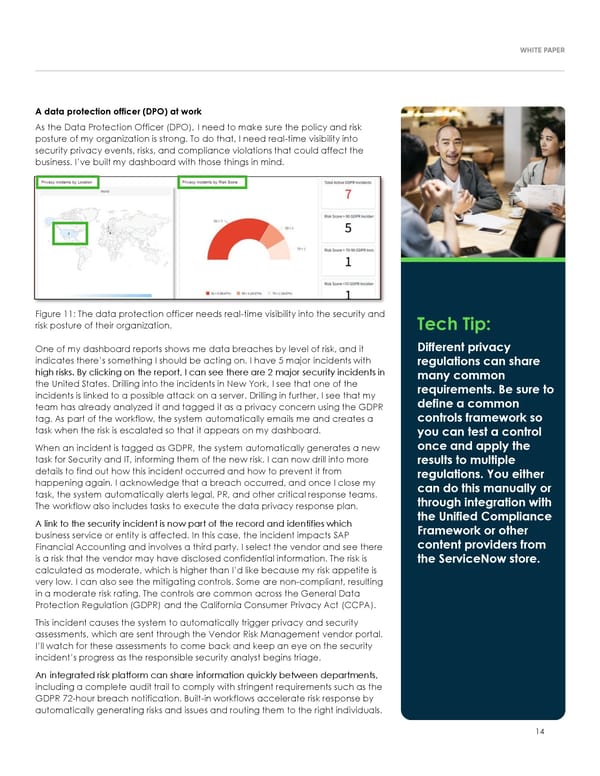
A data protection officer (DPO) at work As the Data Protection Officer (DPO), I need to make sure the policy and risk posture of my organization is strong. To do that, I need real-time visibility into security privacy events, risks, and compliance violations that could affect the business. I9ve built my dashboard with those things in mind. Figure 11: The data protection officer needs real-time visibility into the security and risk posture of their organization. Tech Tip: One of my dashboard reports shows me data breaches by level of risk, and it Different privacy indicates there9s something I should be acting on. I have 5 major incidents with regulations can share high risks. By clicking on the report, I can see there are 2 major security incidents in many common the United States. Drilling into the incidents in New York, I see that one of the requirements. Be sure to incidents is linked to a possible attack on a server. Drilling in further, I see that my define a common team has already analyzed it and tagged it as a privacy concern using the GDPR controls framework so tag. As part of the workflow, the system automatically emails me and creates a task when the risk is escalated so that it appears on my dashboard. you can test a control When an incident is tagged as GDPR, the system automatically generates a new once and apply the task for Security and IT, informing them of the new risk. I can now drill into more results to multiple details to find out how this incident occurred and how to prevent it from regulations. You either happening again. I acknowledge that a breach occurred, and once I close my can do this manually or task, the system automatically alerts legal, PR, and other critical response teams. through integration with The workflow also includes tasks to execute the data privacy response plan. the Unified Compliance A link to the security incident is now part of the record and identifies which Framework or other business service or entity is affected. In this case, the incident impacts SAP content providers from Financial Accounting and involves a third party. I select the vendor and see there is a risk that the vendor may have disclosed confidential information. The risk is the ServiceNow store. calculated as moderate, which is higher than I9d like because my risk appetite is very low. I can also see the mitigating controls. Some are non-compliant, resulting in a moderate risk rating. The controls are common across the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). This incident causes the system to automatically trigger privacy and security assessments, which are sent through the Vendor Risk Management vendor portal. I9ll watch for these assessments to come back and keep an eye on the security incident9s progress as the responsible security analyst begins triage. An integrated risk platform can share information quickly between departments, including a complete audit trail to comply with stringent requirements such as the GDPR 72-hour breach notification. Built-in workflows accelerate risk response by automatically generating risks and issues and routing them to the right individuals. 14
 Integrated Risk and Compliance Page 13 Page 15
Integrated Risk and Compliance Page 13 Page 15