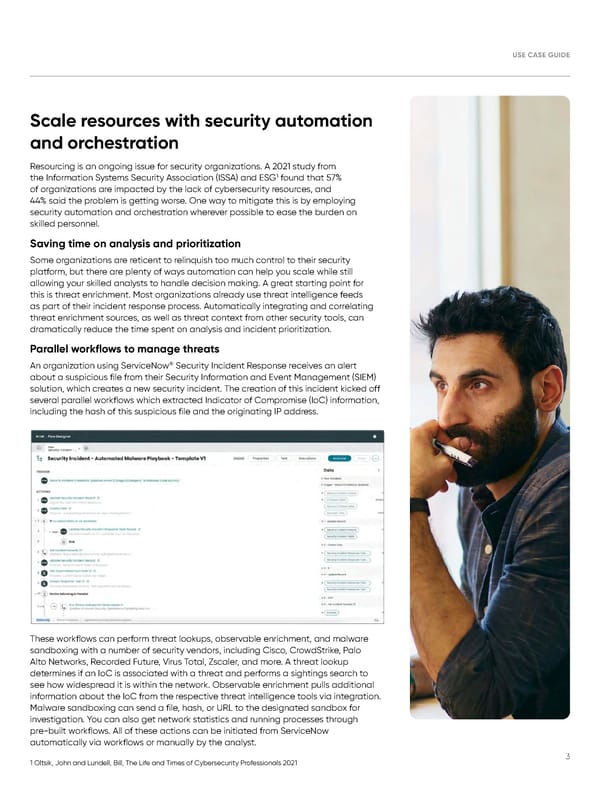
USE CASE GUIDE Scale resources with security automation and orchestration Resourcing is an ongoing issue for security organizations. A 2021 study from 1 the Information Systems Security Association (ISSA) and ESG found that 57% of organizations are impacted by the lack of cybersecurity resources, and 44% said the problem is getting worse. One way to mitigate this is by employing security automation and orchestration wherever possible to ease the burden on skilled personnel. Saving time on analysis and prioritization Some organizations are reticent to relinquish too much control to their security platform, but there are plenty of ways automation can help you scale while still allowing your skilled analysts to handle decision making. A great starting point for this is threat enrichment. Most organizations already use threat intelligence feeds as part of their incident response process. Automatically integrating and correlating threat enrichment sources, as well as threat context from other security tools, can dramatically reduce the time spent on analysis and incident prioritization. Parallel workflows to manage threats ® An organization using ServiceNow Security Incident Response receives an alert about a suspicious file from their Security Information and Event Management (SIEM) solution, which creates a new security incident. The creation of this incident kicked off several parallel workflows which extracted Indicator of Compromise (IoC) information, including the hash of this suspicious file and the originating IP address. These workflows can perform threat lookups, observable enrichment, and malware sandboxing with a number of security vendors, including Cisco, CrowdStrike, Palo Alto Networks, Recorded Future, Virus Total, Zscaler, and more. A threat lookup determines if an IoC is associated with a threat and performs a sightings search to see how widespread it is within the network. Observable enrichment pulls additional information about the IoC from the respective threat intelligence tools via integration. Malware sandboxing can send a file, hash, or URL to the designated sandbox for investigation. You can also get network statistics and running processes through pre-built workflows. All of these actions can be initiated from ServiceNow automatically via workflows or manually by the analyst. 1 Oltsik, John and Lundell, Bill, The Life and Times of Cybersecurity Professionals 2021 3
 Security Operations Page 2 Page 4
Security Operations Page 2 Page 4