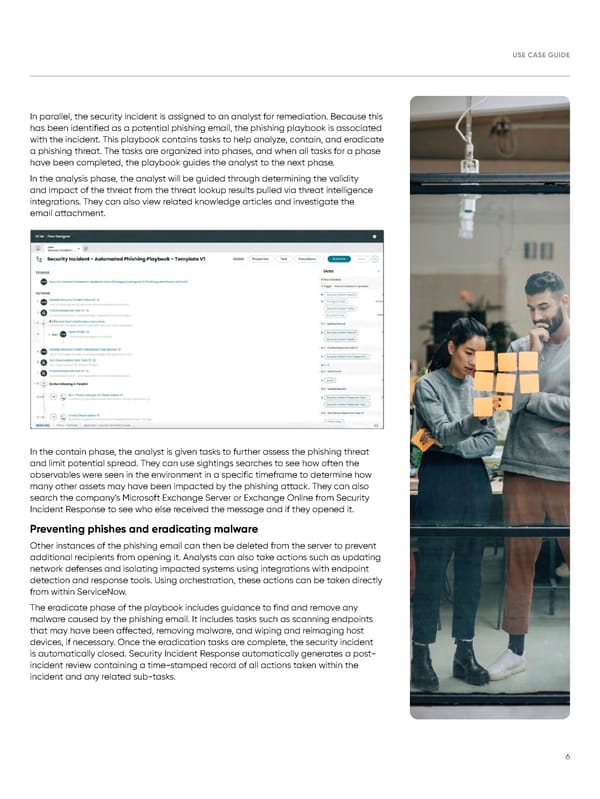
USE CASE GUIDE In parallel, the security incident is assigned to an analyst for remediation. Because this has been identified as a potential phishing email, the phishing playbook is associated with the incident. This playbook contains tasks to help analyze, contain, and eradicate a phishing threat. The tasks are organized into phases, and when all tasks for a phase have been completed, the playbook guides the analyst to the next phase. In the analysis phase, the analyst will be guided through determining the validity and impact of the threat from the threat lookup results pulled via threat intelligence integrations. They can also view related knowledge articles and investigate the email attachment. In the contain phase, the analyst is given tasks to further assess the phishing threat and limit potential spread. They can use sightings searches to see how often the observables were seen in the environment in a specific timeframe to determine how many other assets may have been impacted by the phishing attack. They can also search the company’s Microsoft Exchange Server or Exchange Online from Security Incident Response to see who else received the message and if they opened it. Preventing phishes and eradicating malware Other instances of the phishing email can then be deleted from the server to prevent additional recipients from opening it. Analysts can also take actions such as updating network defenses and isolating impacted systems using integrations with endpoint detection and response tools. Using orchestration, these actions can be taken directly from within ServiceNow. The eradicate phase of the playbook includes guidance to find and remove any malware caused by the phishing email. It includes tasks such as scanning endpoints that may have been affected, removing malware, and wiping and reimaging host devices, if necessary. Once the eradication tasks are complete, the security incident is automatically closed. Security Incident Response automatically generates a post- incident review containing a time-stamped record of all actions taken within the incident and any related sub-tasks. 6
 Security Operations Page 5 Page 7
Security Operations Page 5 Page 7