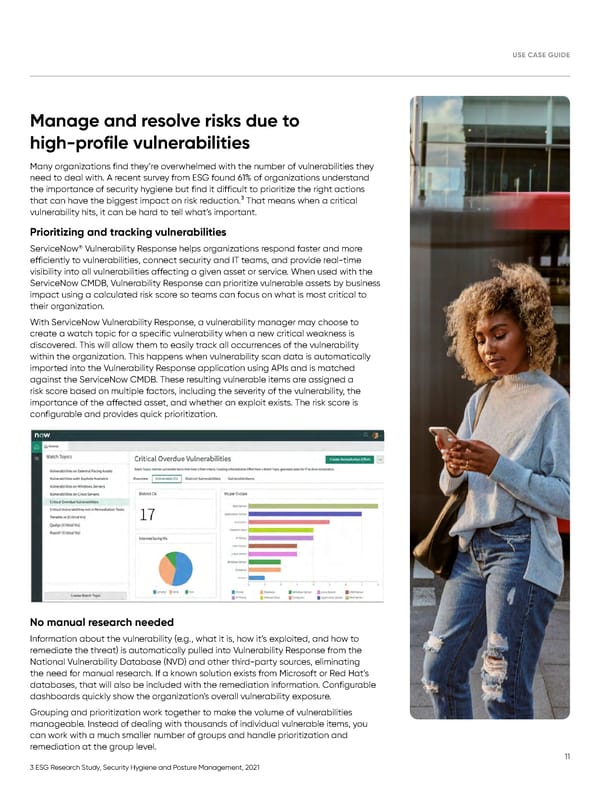
USE CASE GUIDE Manage and resolve risks due to high-profile vulnerabilities Many organizations find they’re overwhelmed with the number of vulnerabilities they need to deal with. A recent survey from ESG found 61% of organizations understand the importance of security hygiene but find it difficult to prioritize the right actions that can have the biggest impact on risk reduction.3 That means when a critical vulnerability hits, it can be hard to tell what’s important. Prioritizing and tracking vulnerabilities ® ServiceNow Vulnerability Response helps organizations respond faster and more efficiently to vulnerabilities, connect security and IT teams, and provide real-time visibility into all vulnerabilities affecting a given asset or service. When used with the ServiceNow CMDB, Vulnerability Response can prioritize vulnerable assets by business impact using a calculated risk score so teams can focus on what is most critical to their organization. With ServiceNow Vulnerability Response, a vulnerability manager may choose to create a watch topic for a specific vulnerability when a new critical weakness is discovered. This will allow them to easily track all occurrences of the vulnerability within the organization. This happens when vulnerability scan data is automatically imported into the Vulnerability Response application using APIs and is matched against the ServiceNow CMDB. These resulting vulnerable items are assigned a risk score based on multiple factors, including the severity of the vulnerability, the importance of the affected asset, and whether an exploit exists. The risk score is configurable and provides quick prioritization. No manual research needed Information about the vulnerability (e.g., what it is, how it’s exploited, and how to remediate the threat) is automatically pulled into Vulnerability Response from the National Vulnerability Database (NVD) and other third-party sources, eliminating the need for manual research. If a known solution exists from Microsoft or Red Hat’s databases, that will also be included with the remediation information. Configurable dashboards quickly show the organization’s overall vulnerability exposure. Grouping and prioritization work together to make the volume of vulnerabilities manageable. Instead of dealing with thousands of individual vulnerable items, you can work with a much smaller number of groups and handle prioritization and remediation at the group level. 11 3 ESG Research Study, Security Hygiene and Posture Management, 2021
 Security Operations Page 10 Page 12
Security Operations Page 10 Page 12