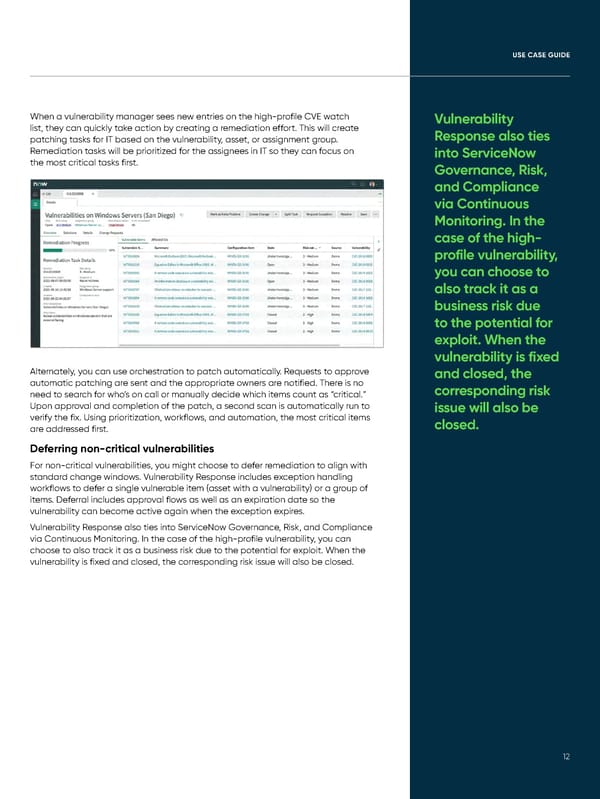
UUSE CSE CAASE GUSE GUIIDDEE When a vulnerability manager sees new entries on the high-profile CVE watch Vulnerability list, they can quickly take action by creating a remediation effort. This will create Response also ties patching tasks for IT based on the vulnerability, asset, or assignment group. Remediation tasks will be prioritized for the assignees in IT so they can focus on into ServiceNow the most critical tasks first. Governance, Risk, and Compliance via Continuous Monitoring. In the case of the high- profile vulnerability, you can choose to also track it as a business risk due to the potential for exploit. When the vulnerability is fixed Alternately, you can use orchestration to patch automatically. Requests to approve and closed, the automatic patching are sent and the appropriate owners are notified. There is no corresponding risk need to search for who’s on call or manually decide which items count as “critical.” Upon approval and completion of the patch, a second scan is automatically run to issue will also be verify the fix. Using prioritization, workflows, and automation, the most critical items closed. are addressed first. Deferring non-critical vulnerabilities For non-critical vulnerabilities, you might choose to defer remediation to align with standard change windows. Vulnerability Response includes exception handling workflows to defer a single vulnerable item (asset with a vulnerability) or a group of items. Deferral includes approval flows as well as an expiration date so the vulnerability can become active again when the exception expires. Vulnerability Response also ties into ServiceNow Governance, Risk, and Compliance via Continuous Monitoring. In the case of the high-profile vulnerability, you can choose to also track it as a business risk due to the potential for exploit. When the vulnerability is fixed and closed, the corresponding risk issue will also be closed. 1212
 Security Operations Page 11 Page 13
Security Operations Page 11 Page 13