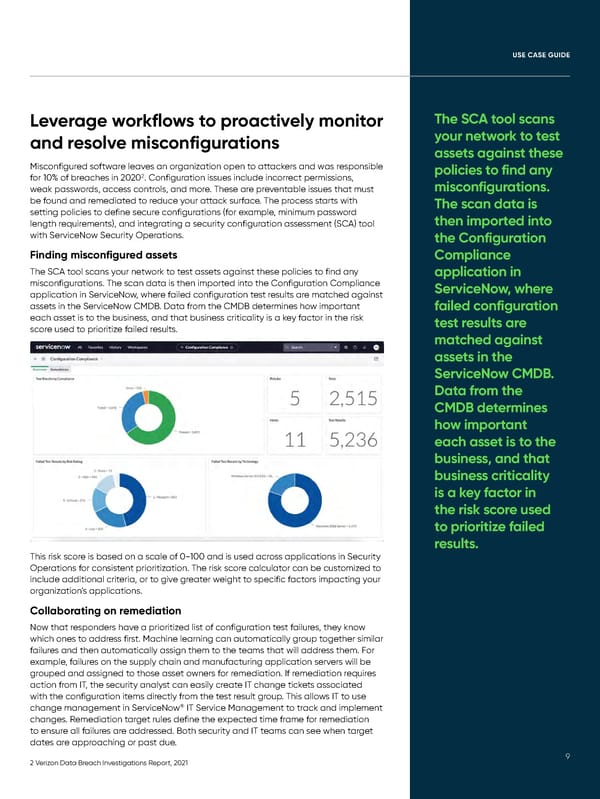
UUSE CSE CAASE GUSE GUIIDDEE Leverage workflows to proactively monitor The SCA tool scans and resolve misconfigurations your network to test assets against these Misconfigured software leaves an organization open to attackers and was responsible policies to find any for 10% of breaches in 20202. Configuration issues include incorrect permissions, weak passwords, access controls, and more. These are preventable issues that must misconfigurations. be found and remediated to reduce your attack surface. The process starts with The scan data is setting policies to define secure configurations (for example, minimum password then imported into length requirements), and integrating a security configuration assessment (SCA) tool with ServiceNow Security Operations. the Configuration Finding misconfigured assets Compliance The SCA tool scans your network to test assets against these policies to find any application in misconfigurations. The scan data is then imported into the Configuration Compliance ServiceNow, where application in ServiceNow, where failed configuration test results are matched against assets in the ServiceNow CMDB. Data from the CMDB determines how important failed configuration each asset is to the business, and that business criticality is a key factor in the risk test results are score used to prioritize failed results. matched against assets in the ServiceNow CMDB. Data from the CMDB determines how important each asset is to the business, and that business criticality is a key factor in the risk score used to prioritize failed results. This risk score is based on a scale of 0-100 and is used across applications in Security Operations for consistent prioritization. The risk score calculator can be customized to include additional criteria, or to give greater weight to specific factors impacting your organization’s applications. Collaborating on remediation Now that responders have a prioritized list of configuration test failures, they know which ones to address first. Machine learning can automatically group together similar failures and then automatically assign them to the teams that will address them. For example, failures on the supply chain and manufacturing application servers will be grouped and assigned to those asset owners for remediation. If remediation requires action from IT, the security analyst can easily create IT change tickets associated with the configuration items directly from the test result group. This allows IT to use change management in ServiceNow® IT Service Management to track and implement changes. Remediation target rules define the expected time frame for remediation to ensure all failures are addressed. Both security and IT teams can see when target dates are approaching or past due. 2 Verizon Data Breach Investigations Report, 2021 99
 Security Operations Page 8 Page 10
Security Operations Page 8 Page 10