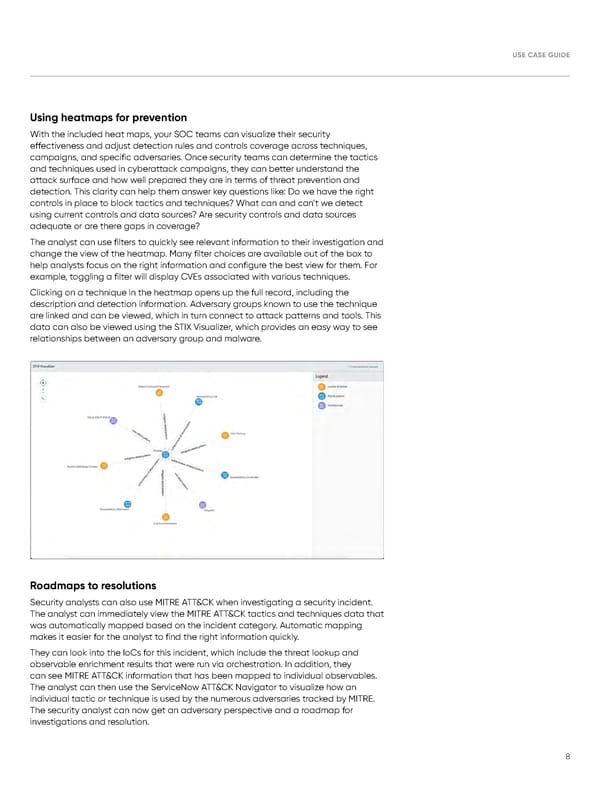
USE CASE GUIDE Using heatmaps for prevention With the included heat maps, your SOC teams can visualize their security effectiveness and adjust detection rules and controls coverage across techniques, campaigns, and specific adversaries. Once security teams can determine the tactics and techniques used in cyberattack campaigns, they can better understand the attack surface and how well prepared they are in terms of threat prevention and detection. This clarity can help them answer key questions like: Do we have the right controls in place to block tactics and techniques? What can and can’t we detect using current controls and data sources? Are security controls and data sources adequate or are there gaps in coverage? The analyst can use filters to quickly see relevant information to their investigation and change the view of the heatmap. Many filter choices are available out of the box to help analysts focus on the right information and configure the best view for them. For example, toggling a filter will display CVEs associated with various techniques. Clicking on a technique in the heatmap opens up the full record, including the description and detection information. Adversary groups known to use the technique are linked and can be viewed, which in turn connect to attack patterns and tools. This data can also be viewed using the STIX Visualizer, which provides an easy way to see relationships between an adversary group and malware. Roadmaps to resolutions Security analysts can also use MITRE ATT&CK when investigating a security incident. The analyst can immediately view the MITRE ATT&CK tactics and techniques data that was automatically mapped based on the incident category. Automatic mapping makes it easier for the analyst to find the right information quickly. They can look into the IoCs for this incident, which include the threat lookup and observable enrichment results that were run via orchestration. In addition, they can see MITRE ATT&CK information that has been mapped to individual observables. The analyst can then use the ServiceNow ATT&CK Navigator to visualize how an individual tactic or technique is used by the numerous adversaries tracked by MITRE. The security analyst can now get an adversary perspective and a roadmap for investigations and resolution. 8
 Security Operations Page 7 Page 9
Security Operations Page 7 Page 9