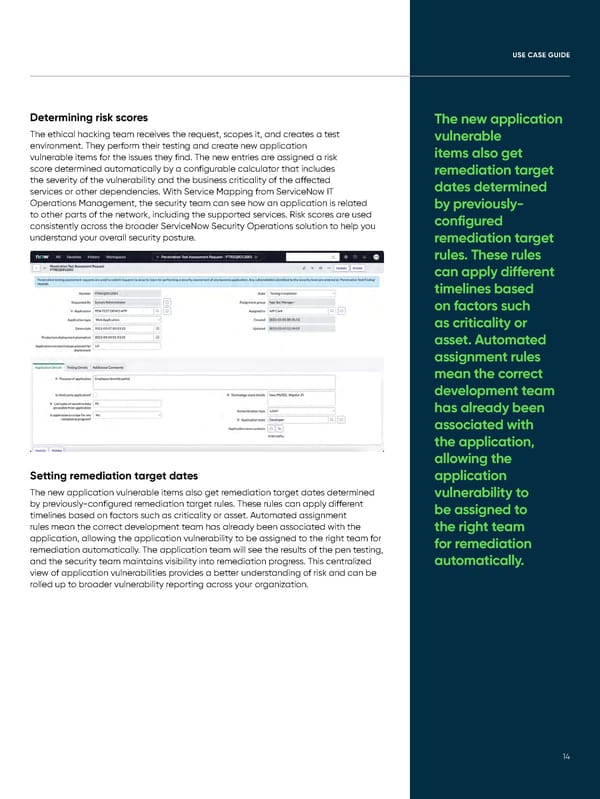
UUSE CSE CAASE GUSE GUIIDDEE Determining risk scores The new application The ethical hacking team receives the request, scopes it, and creates a test vulnerable environment. They perform their testing and create new application items also get vulnerable items for the issues they find. The new entries are assigned a risk score determined automatically by a configurable calculator that includes remediation target the severity of the vulnerability and the business criticality of the affected dates determined services or other dependencies. With Service Mapping from ServiceNow IT Operations Management, the security team can see how an application is related by previously- to other parts of the network, including the supported services. Risk scores are used configured consistently across the broader ServiceNow Security Operations solution to help you understand your overall security posture. remediation target rules. These rules can apply different timelines based on factors such as criticality or asset. Automated assignment rules mean the correct development team has already been associated with the application, allowing the Setting remediation target dates application The new application vulnerable items also get remediation target dates determined vulnerability to by previously-configured remediation target rules. These rules can apply different be assigned to timelines based on factors such as criticality or asset. Automated assignment rules mean the correct development team has already been associated with the the right team application, allowing the application vulnerability to be assigned to the right team for for remediation remediation automatically. The application team will see the results of the pen testing, and the security team maintains visibility into remediation progress. This centralized automatically. view of application vulnerabilities provides a better understanding of risk and can be rolled up to broader vulnerability reporting across your organization. 1414
 Security Operations Page 13 Page 15
Security Operations Page 13 Page 15