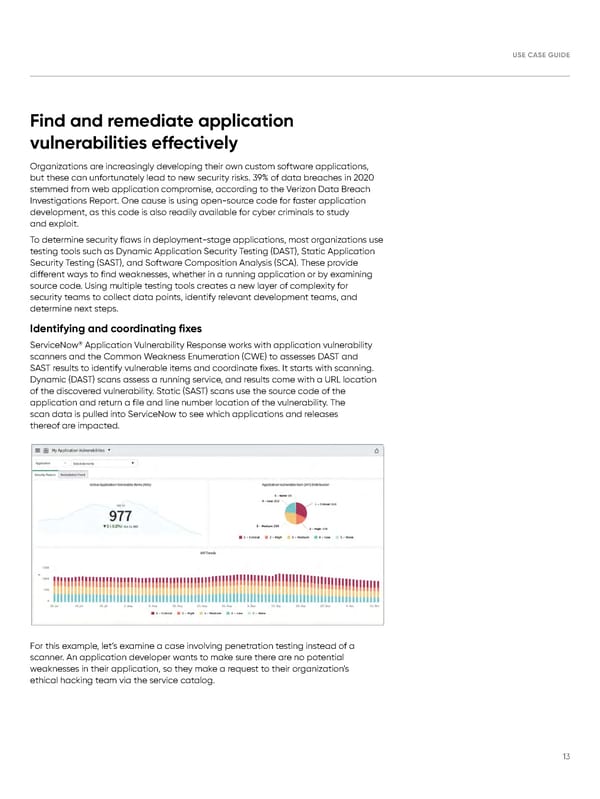
USE CASE GUIDE Find and remediate application vulnerabilities effectively Organizations are increasingly developing their own custom software applications, but these can unfortunately lead to new security risks. 39% of data breaches in 2020 stemmed from web application compromise, according to the Verizon Data Breach Investigations Report. One cause is using open-source code for faster application development, as this code is also readily available for cyber criminals to study and exploit. To determine security flaws in deployment-stage applications, most organizations use testing tools such as Dynamic Application Security Testing (DAST), Static Application Security Testing (SAST), and Software Composition Analysis (SCA). These provide different ways to find weaknesses, whether in a running application or by examining source code. Using multiple testing tools creates a new layer of complexity for security teams to collect data points, identify relevant development teams, and determine next steps. Identifying and coordinating fixes ® ServiceNow Application Vulnerability Response works with application vulnerability scanners and the Common Weakness Enumeration (CWE) to assesses DAST and SAST results to identify vulnerable items and coordinate fixes. It starts with scanning. Dynamic (DAST) scans assess a running service, and results come with a URL location of the discovered vulnerability. Static (SAST) scans use the source code of the application and return a file and line number location of the vulnerability. The scan data is pulled into ServiceNow to see which applications and releases thereof are impacted. For this example, let’s examine a case involving penetration testing instead of a scanner. An application developer wants to make sure there are no potential weaknesses in their application, so they make a request to their organization’s ethical hacking team via the service catalog. 13
 Security Operations Page 12 Page 14
Security Operations Page 12 Page 14